| POD parameters : | OpenStack Group-1 | user0 | aio110 | 10.1.64.110 | compute120 | 10.1.64.120 | [email protected] |
| User | aioX | computeY | Network & Allocation Pool |
|
user0
ssh : [email protected]
vnc : lab.onecloudinc.com:5900
|
aio110
eth0 : 10.1.64.110
eth1 : 10.1.65.110
eth2 : ext-net
Netmask : 255.255.255.0
Gateway : 10.1.64.1
|
compute120
eth0 : 10.1.64.120
eth1 : 10.1.65.120
eth2 : ext-net
Netmask : 255.255.255.0
|
Float Range : 10.1.65.00 – 10.1.65.00
Network : 10.1.65.0/24
Gateway : 10.1.65.1
DNS : 10.1.1.92
|
Introduction
Linux Containers have emerged as a key open source application packaging and delivery technology, combining lightweight application isolation with the flexibility of image-based deployment methods. Developers have rapidly embraced Linux Containers because they simplify and accelerate application deployment, while many PaaS platforms are built around Linux container technology. Linux Containers are implemented using core technologies such as Control Groups (cGroups), SELinux and namespaces, enabling secure multi-tenancy and reducing the potential for security exploits.
1. Linux Container and Docker
Linux containers tend to speed up application development, because user can build once and run on any infrastructure. Infrastructure can include bare-metal servers, virtual machines, public clouds, and network devices.
1.1 Linux Container
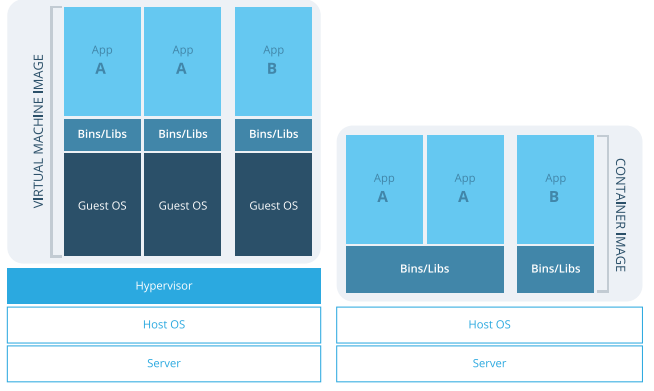
In a normal virtualized environment, virtual machines run on top of a physical machine with the aid of a hypervisor (e.g. Xen, Hyper-V). Containers run on user space on top of an operating system’s kernel. Each container has its own isolated user space, and it’s possible to run many different containers on one host. Containers are isolated in a host using two Linux kernel features: Namespaces and Control Groups.
1.2 Docker
Docker is a container engine that uses the Linux Kernel features to make containers on top of an OS and automates app deployment on the container. It provides a lightweight environment to run app code in order to create a more efficient workflow for moving user app through the life cycle. It runs on a client-server architecture. The Docker Daemon is responsible for all the actions related to the containers, and this daemon gets the commands from the Docker client through cli or REST APIs.
2. Linux Container Concepts
Linux Container is an operating-system-level virtualization method for running multiple isolated Linux systems (containers) on a control host using a single Linux kernel.
2.1 Container use cases
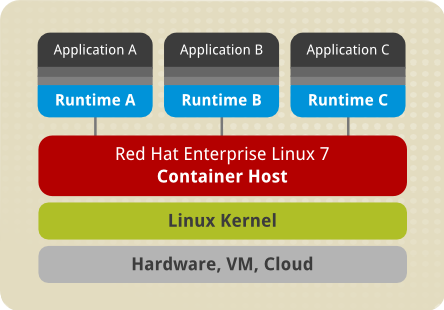
Image-based containers package applications with individual runtime stacks, making the resultant containers independent from the host operating system. This makes it possible to run several instances of an application, each developed for a different platform. This is possible because the container run time and the application run time are deployed in the form of an image. For example, Runtime A could refer to Red Hat Enterprise Linux 6.5, Runtime B could refer to version 6.6 and so on.
Image-based containers allow us to host multiple instances and versions of an application, with minimal overhead and increased flexibility. Such containers are not tied to the host-specific configuration, which makes them portable.
2.2 Containers Vs Virtualization
Virtualization:
- Virtualization enables booting full operating systems of different kinds, even non-Linux systems. The resource-hungry nature of virtual machines (as compared to containers) means that the number of virtual machines that can be run on a host is lower than the number of containers that can be run on the same host.
- Running separate kernel instances generally provides separation and security. The unexpected termination of one of the kernels does not disable the whole system.
- Guest virtual machine is isolated from host changes, which allows to run different versions of the same application on the host and virtual machine. KVM also provides many useful features such as live migration.
Linux Containers:
- Linux Containers are designed to support isolation of one or more applications.
- System-wide changes are visible in each container. For example, if user upgrade an application on the host machine, this change will apply to all sandboxes that run instances of this application.
- Since containers are lightweight, a large number of them can run simultaneously on a host machine. The theoretical maximum is 6000 containers and 12,000 bind mounts of root file system directories.
2.3 Implementations
Linux Containers are built around core mature Linux technologies:
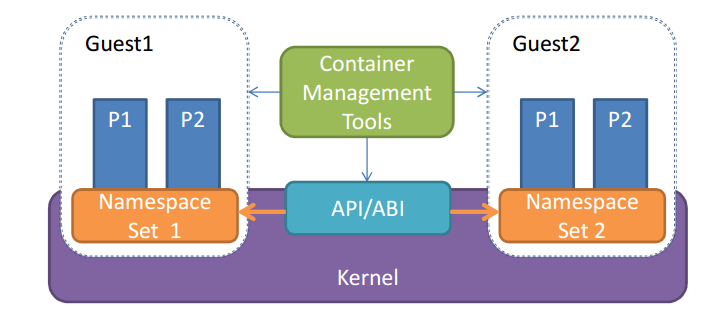
- Namespaces: Kernel namespaces isolate containers. Namespaces main outcomes are avoiding visibility between containers and containing faults. Some of the domains of isolation provided by Namespaces are:
- pid (processes)
- net (network interfaces, routing)
- ipc (System V interprocess communication [IPC])
- mnt (mount points, file systems)
- uts (host name)
- user (user IDs [UIDs])
- Control groups (cgroups): Control groups offer mechanisms for measuring and limiting resource usage for groups of processes, such as CPU, memory, and I/O. This helps containers stay within the resource footprint allocated to them.
- Security-Enhanced Linux (SELinux): It is an implementation of a mandatory access control (MAC) mechanism, multi-level security (MLS), and multi-category security (MCS) in the Linux kernel. The sVirt project builds upon SELinux and integrates with Libvirt to provide a MAC framework for virtual machines and containers.